
Minimum settings to protect your WordPress site
I wrote about how to attack WP, but if you take the minimum security measures to build a WP site, you won’t end up in the same situation as in …

I was casually browsing youtube when I came across the following video. The content of the video explained that the “recaptcha v2” “I’m not a robot” security check is the most difficult for robots.
No, that’s not possible! This video was published on “2021/04/13”, so it’s not from the old days when “I’m not a robot” was considered solid. v3 and Enterprise of recaptcha already existed in 2021, and this “I’m not a robot This “I’m not a robot” thing is old and shoddy. It seems to me that the author of this video has probably made the wrong video.
So I actually tried to see if this “I’m not a robot” operation is really the most difficult for robots.
By the way, please don’t abuse the following operation. If you do this to any site, the identity of the abuser will be revealed, and you may be punished for a criminal act.
Prepare a recaptcha in WP Contact Form 7. By the way, CF7 requires an older version to set up V2, so I installed CF7 version 4.9 series and created the following page. (Of course, the API key is also set correctly for production use.)
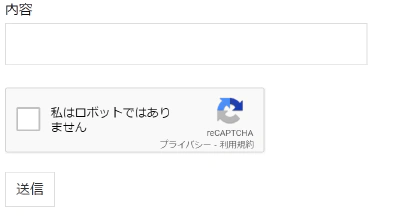
I put a string in the content and send it so that an email is sent. In other words, if the robot accesses this page and sends it, and the mail is delivered, it is a success.
Well, first of all, access that is not through a browser will naturally be judged as not being human. In fact, when I retrieved the page in question using cURL, it seemed that the “I’m not a robot” part was described using JS and an iframe, so it would be impossible to use only normal HTTP requests. So, I will try the following strategy to control the robot.
In the meantime, write code that satisfies these two requirements and try it out. If this doesn’t work, I’ll try adding more complex operations.
If you want to install Chromium easily, Puppeteer seems to be an easy way to do it. (Assuming nodejs is already installed)
npm install puppeteer --save
This is all you need to do to scrape using headless chromium. So easy.
By the way, with the following code, it is easy for the robot to access a website from a browser and save it with a screenshot of its state. So, you can visually check the status of the robot operation.
const puppeteer = require('puppeteer');
(async () => {
const browser = await puppeteer.launch();
const page = await browser.newPage();
await page.goto('Page URL');
await page.screenshot({path: 'result.png'});
await browser.close();
})();
Incidentally, when I let the robot access the prepared page in the usual way and press the send button, the scribe was caught by security and an error appeared as shown below.
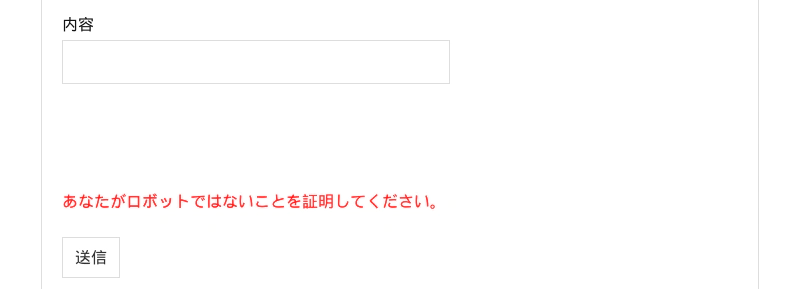
Hmm. So this is the power of reCaptcha…
I immediately created a file called app.js and did the following programming.
const puppeteer = require('puppeteer');
function delay(time) {
return new Promise(function(resolve) {
setTimeout(resolve, time)
});
}
(async () => {
const browser = await puppeteer.launch();
const page = await browser.newPage();
await page.goto('Page URL');
await delay(2312); // You can change it to a random number.
await page.type('input[name="your-subject"]', 'I am a ROBOT!'); //Write the body of the email.
await delay(2433); // You can change it to a random number.
await page.frames().find(f => f.url().indexOf('recaptcha') != -1).click('div.recaptcha-checkbox-border');
await delay(1877); // You can change it to a random number.
await page.screenshot({path: 'result.png'});
await page.click('input[type="submit"]');
await browser.close();
})();
Then run the following command.
node app.js
Then the screenshot of puppeteer was as follows.
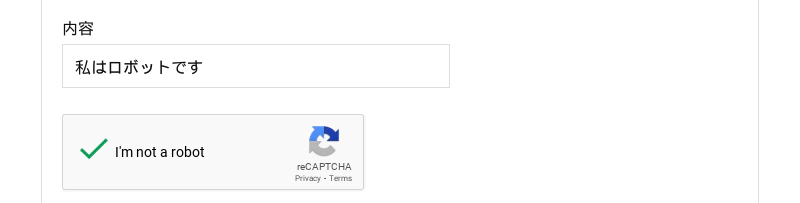
Of course, the email was sent correctly. (The robot was able to press the “send” button.)
With less than 20 lines of code, the robot was easily able to become a human. By the way, it succeeded even when executed from within a server in the US region. This means that it is possible to break through from overseas.
Hmmm. Isn’t that too easy? It only took me about 15 minutes to create the above code. I thought it would be too easy to fail at first, so I thought I’d make the scrolling, cursors, and clicks work randomly to make it more human-like.
That means it’s easy to programmatically access and make tens of thousands of attempts against the login and registration screens with this “I’m not a robot” on it. (That’s a crime! It’s a criminal act!)
As of 2021, there is an Enterprise version of this reCaptcha, which is probably more accurate. But you won’t see the “I’m not a robot” button in v3 or Enterprise. Also, I wouldn’t dare do it, but it seems that v3 and Enterprise can be broken through with the same idea.
Um, “I’m not a robot” is the strongest is a lie. The strongest is an exaggeration, since robots have been able to break through even with simple programming like the above.
And at the same time, I don’t trust security measures with something like this. do you think that because you are doing wait or something in chromium, it takes longer to execute one time, and thus you can avoid tens of thousands of attempts? If you start hundreds of containers and execute each of the above nodes in parallel, you can easily execute hundreds of thousands of times.
So, this time, I tried to break through “I’m not a robot” easily with a robot.

I wrote about how to attack WP, but if you take the minimum security measures to build a WP site, you won’t end up in the same situation as in …

Somehow, being bad can be fascinating. Probably anyone who was born between the 1970s and early 1990s and touched a PC during their school days has …